The digital world is like a vast city, with highways, bridges, and tunnels flowing through it. Behind the scenes, network administrators act as the architects and traffic controllers, managing communication, security, and efficiency. Without them, businesses, hospitals, and industries would face digital gridlock.
Do you want to connect with the world? If so, Florida National University (FNU) offers a Network Systems Administrator degree program that provides the skills and training needed to design, manage, and secure these critical networks. Whether you are looking to build the next great digital infrastructure or protect valuable data, FNU’s program is your gateway to a career in networking.
What Does a Network System Administrator Do?
A network system administrator manages and maintains an organization’s IT infrastructure. Their job includes setting up networks, troubleshooting issues, and securing systems from cyber threats. If you are considering a career in this field, network administrator training is essential for acquiring the necessary skills to maintain secure and efficient networks.
Network Setup and Configuration
Network administrators design, configure, and install the hardware and software needed for a company’s internal and external networks. They facilitate smooth communication between devices, servers, and external connections. For example, a company opening a new office needs a fully operational network. The administrator installs routers, switches, and firewalls, then configures IP addressing, VLANs, and security settings for proper connectivity.
Monitoring Network Performance
Continuous monitoring is crucial to ensure that network traffic flows smoothly without bottlenecks or failures. Network systems administrators utilize specialized software to track performance metrics and identify potential issues before they escalate into problems. In situations where employees complain about slow internet speeds, a network administrator can use tools such as SolarWinds or Wireshark to analyze traffic and identify congestion.
Troubleshooting Network Issues
Network failures can disrupt business operations. Network systems administrators must quickly diagnose and fix connectivity issues, hardware failures, and software misconfigurations. If a department suddenly loses access to a shared drive, the administrator checks firewall rules, user permissions, and connection logs to find the root cause.
Managing User Access and Permissions
For the network’s data security, network systems administrators set up user accounts, assign permissions, and enforce access policies. For example, a new employee needs access to the company’s internal systems. The administrator creates an account in Active Directory, assigns the correct role-based permissions, and enables multi-factor authentication (MFA).
Implementing Network Security Measures
Protecting the network from cyber threats is a top priority. Network systems administrators implement firewalls, intrusion detection systems, and encryption to prevent attacks. After a company experiences a phishing attack, the network systems administrator may set up email filtering and enhance firewall rules to block suspicious traffic.
Software and Hardware Updates
Regular updates prevent vulnerabilities and improve system performance. Network systems administrators must track patches, firmware updates, and software versions to ensure optimal system performance. On occasion, Microsoft releases a security patch for Windows servers. The network systems administrator can test it in a lab environment before deploying it to production servers.
Maintaining Backup and Recovery Systems
Backups help recover data in case of system failures or cyberattacks. Network systems administrators set up and regularly test backup solutions. For example, after a ransomware attack encrypts company files, the network systems administrator restores data from the most recent backup.
Supporting Remote and Onsite Employees
Many businesses have remote teams that require secure access to internal networks. Network systems administrators set up VPNs, remote desktop services, and cloud-based solutions. For example, an employee working from home needs access to internal files. The network systems administrator can set up a secure VPN connection and proper authentication.
Documenting Network Configurations and Procedures
Proper documentation helps IT teams understand network setups and troubleshoot problems efficiently. A network systems administrator can create a detailed network diagram showing IP ranges, switch configurations, and security policies.
Planning for Network Expansion and Upgrades
Businesses grow, and network infrastructure must scale accordingly. Network systems administrators plan for upgrades to handle increased traffic and new technologies. For example, a growing company may need to upgrade from a 1 Gbps to a 10 Gbps network to support more employees and cloud applications.
Why are Network System Administrators Important?
Businesses rely on technology to operate efficiently. There are many reasons why a network system administrator is important. Here are a few of those important reasons:
Keeping Networks Running Smoothly
Network administrators install, configure, and maintain hardware and software that keep systems online. They monitor performance, troubleshoot issues, and upgrade infrastructure to prevent failures. Employees may struggle with slow connections, dropped calls, or lost data if proper network management is not in place.
Protecting Businesses from Cyber Threats
Cyberattacks, malware, and data breaches pose significant risks to organizations. Network systems administrators implement firewalls, encryption, and access controls to protect sensitive information. They also monitor traffic for unusual activity, preventing unauthorized access. The good news is that network administrator training covers security protocols, risk management, and best practices to safeguard systems.
Minimizing Downtime and Improving Productivity
Network failures can halt business operations, causing lost revenue and frustration. Network systems administrators quickly diagnose and fix problems, reducing downtime. They also develop backup and disaster recovery plans to prevent data loss.
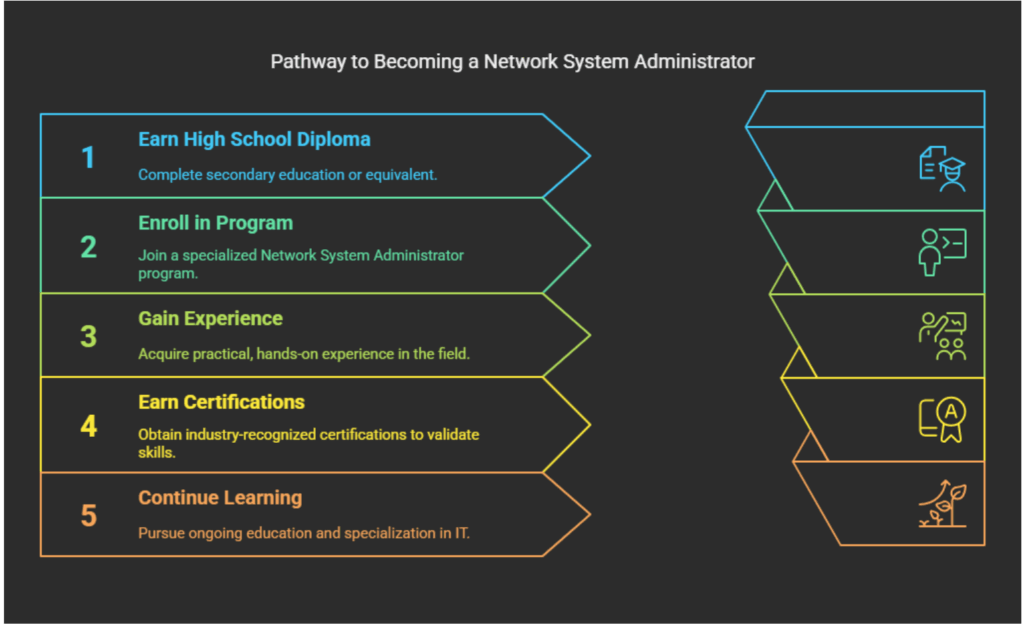
How Do You Become a Network System Administrator?
If you want to become a network system administrator, follow this step-by-step guide to gain the skills, experience, and certifications needed for a successful career.
Step 1: Earn a High School Diploma or Equivalent
This offers a strong foundation in math, science, and computer skills, which is essential. You will also take courses in computer science or IT, if available, and develop problem-solving and critical-thinking skills.
Step 2: Enroll in FNU’s Network System Administrator Program
Florida National University offers a Network System Administrator program that provides hands-on training. During this program, you learn network setup, troubleshooting, cybersecurity, and server management. You also become familiar with operating systems, cloud computing, and virtualization.
Step 3: Gain Hands-On Experience
This is your opportunity to practice configuring routers, switches, and firewalls. Hands-on experience can be gained in virtual labs or by setting up a home network for testing purposes. You will be able to apply the skills learned at FNU through internships or entry-level IT roles.
Step 4: Earn Industry Certifications
FNU’s program helps prepare for key IT certifications, including:
- CompTIA Network+ – Covers networking basics.
- Cisco CCNA – Focuses on network infrastructure and security.
- Microsoft Azure Administrator – Specializes in cloud-based networking.
Step 5: Continue Learning and Specializing
This helps you gain experience in network security, cloud computing, or system administration. You may also be able to pursue advanced certifications, such as CompTIA Security+ or Cisco CCNP. This will also help you stay updated with the latest IT trends and technologies.
What Do You Learn During Network Administrator Training?
Florida National University offers a comprehensive Associate of Science in Networking Systems Administrator program to help you learn the essential skills for designing, installing, configuring, and supporting computer networks. The curriculum combines technical training with a foundational understanding of networking principles. Below is a list of core courses included in the program:
Computer Repair I (Hardware) – A+
This course covers the fundamentals of computer hardware components, including motherboards, processors, memory, storage devices, and power supplies. You learn how to assemble, upgrade, and troubleshoot computer systems. This course also helps you prepare for the CompTIA A+ certification, a key entry-level credential for IT professionals.
Computer Repair II (Software) – A+
A course that focuses on operating system installation, configuration, and troubleshooting. It teaches you about Windows, macOS, and Linux operating systems, with an emphasis on system updates, security patches, and user management. The course also prepares you to resolve software-related issues and optimize system performance.
Networking Essentials – Network+
In this course, you build a foundation for networking concepts, protocols, and standards in modern IT environments. It covers IP addressing, network topology, subnetting, and TCP/IP communication models. By the end of the course, you will be well-prepared for the CompTIA Network+ certification, which is a prerequisite for entry-level network administration roles.
Client Operating System – MCS
In this course, you will focus on Microsoft client operating systems, including Windows installation, configuration, and administration. You will learn about user account management, system security, and network settings. This course prepares you for the Microsoft Certified Solutions Associate (MCSA) certification, which validates Windows administration skills.
Active Directory Service – MCSA
This course teaches Active Directory (AD), the central directory service for managing networked environments in Windows domains. You will learn about user authentication, group policy management, and domain services. By the end of the course, you will be able to implement secure access control policies for businesses.
Server Installation, Configuration, and Administration – MCSA
This course helps you deploy and maintain Windows and Linux servers in enterprise environments. It teaches file sharing, user account creation, server security, and automated system updates. Once the course is completed, you will be ready for system administrator roles and MCSA certification.
Routing Protocols and Concepts – CCENT/CCNA
This course introduces routing protocols, including RIP, OSPF, and EIGRP, which direct traffic within networks. You will learn about subnetting, VLANs, and IP addressing to enhance network efficiency. At the end of the course, you will be ready for Cisco Certified Entry Networking Technician (CCENT) and Cisco Certified Network Associate (CCNA) certifications.
LAN Switching and Wireless Networking – CCENT/CCNA
A course that focuses on switching technologies and wireless network setups in enterprise environments. It teaches you how to use Ethernet switching, VLANs, wireless security protocols (WPA3, WPA2), and network optimization. It also gives you hands-on experience with Cisco networking equipment.
95 Network Administrator Terms You Should Know
Access Control List (ACL) – A set of rules that control network traffic and restrict access to specific users or devices.
Active Directory (AD) – A Microsoft service that manages users, devices, and permissions within a network.
Address Resolution Protocol (ARP) – A protocol used to map an IP address to a MAC address.
Authentication – The process of verifying a user’s identity before granting access to a system.
Bandwidth – The maximum amount of data that can be transmitted over a network in a given period.
Baseline – A standard reference point used to measure network performance and identify anomalies.
Bit Rate – The number of bits transmitted per second in a network connection.
Bridge – A device that connects two or more network segments and filters traffic.
Cache – A temporary storage area for frequently accessed data to improve performance.
Client-Server Model – A network structure where client devices request services from a centralized server.
Cloud Computing – The use of remote servers to store, manage, and process data instead of local servers.
Collision Domain – A network segment where data packets can collide, causing network slowdowns.
Data Packet – A unit of data transmitted over a network.
DHCP (Dynamic Host Configuration Protocol) – A protocol that automatically assigns IP addresses to devices on a network.
DNS (Domain Name System) – Translates domain names into IP addresses.
Dual Stack – A networking method that supports both IPv4 and IPv6 simultaneously.
Encryption – The process of converting data into a coded format to prevent unauthorized access.
Ethernet – A wired networking technology used in local area networks (LANs).
Extranet – A private network that allows external users to access specific internal resources.
Endpoint – Any device connected to a network, such as a computer, smartphone, or printer.
Firewall – A security device or software that controls incoming and outgoing network traffic.
Firmware – Permanent software programmed into hardware devices like routers and switches.
FTP (File Transfer Protocol) – A protocol used to transfer files between computers over a network.
Failover – A backup system that automatically takes over in case of a failure.
Gateway – A device that connects different networks and manages communication between them.
Group Policy – A Windows feature used to manage security and configurations across multiple computers.
Gigabit Ethernet – A network standard that supports speeds of up to 1 Gbps.
GUI (Graphical User Interface) – A visual interface that allows users to interact with software applications.
Hop – The number of routers a data packet passes through before reaching its destination.
Hostname – A unique name assigned to a device on a network.
HTTP (Hypertext Transfer Protocol) – A protocol used for communication between web browsers and servers.
HTTPS (Hypertext Transfer Protocol Secure) – A secure version of HTTP that encrypts data transmission.
IP Address (Internet Protocol Address) – A unique identifier assigned to a device on a network.
Intrusion Detection System (IDS) – A security system that monitors network traffic for suspicious activity.
Intrusion Prevention System (IPS) – A security system that actively blocks potential threats.
ISP (Internet Service Provider) – A company that provides internet access to users.
Jitter – Variations in packet arrival times that can affect network performance and VoIP quality.
Kerberos – A network authentication protocol that uses encryption to secure logins.
LAN (Local Area Network) – A network that connects devices within a limited area, such as an office.
Load Balancer – A device that distributes network traffic evenly across multiple servers.
MAC Address (Media Access Control Address) – A unique identifier assigned to network interfaces.
Malware – Malicious software designed to damage or exploit systems.
Mesh Network – A network topology where devices connect to multiple nodes for redundancy.
NAT (Network Address Translation) – A process that translates private IP addresses into public IP addresses.
Network Topology – The physical or logical layout of a network.
OSI Model (Open Systems Interconnection Model) – A framework that standardizes network communication in seven layers.
Ping – A network utility used to test connectivity between devices.
QoS (Quality of Service) – A technology that prioritizes network traffic for critical applications.
Router – A device that directs data between networks.
Switch – A networking device that connects devices within a LAN and directs data based on MAC addresses.
Remote Desktop Protocol (RDP) – A Microsoft protocol that allows users to connect to remote computers over a network.
Reverse Proxy – A server that retrieves resources from another server on behalf of a client.
Redundancy – The duplication of critical components to ensure network reliability and prevent downtime.
Registry – A database in Windows that stores system and application settings.
Rootkit – A type of malware that hides its presence and provides unauthorized access to a system.
RFID (Radio Frequency Identification) – A technology that uses radio waves for wireless identification and tracking.
Ring Topology – A network configuration where devices are connected in a circular path.
Rogue Access Point – An unauthorized wireless access point that can pose security risks.
Ransomware – A type of malware that encrypts files and demands payment for decryption.
RAID (Redundant Array of Independent Disks) – A method of storing data across multiple hard drives for performance and redundancy.
SAN (Storage Area Network) – A high-speed network that connects storage devices to servers.
Session Hijacking – A cyberattack where an attacker takes control of a user’s session on a network.
Subnet Mask – A number that defines the range of IP addresses in a subnet.
SSH (Secure Shell) – A protocol that provides encrypted remote access to network devices and servers.
SSL/TLS (Secure Sockets Layer/Transport Layer Security) – Protocols that encrypt internet communications for security.
SSID (Service Set Identifier) – The name of a wireless network.
Static IP Address – A manually assigned IP address that does not change.
Syslog – A protocol used for collecting and storing system logs from network devices.
SLA (Service Level Agreement) – A contract that defines performance expectations between a service provider and a client.
SMB (Server Message Block) – A protocol used for sharing files and printers over a network.
TCP/IP (Transmission Control Protocol/Internet Protocol) – The primary protocol suite for communication on the Internet.
TFTP (Trivial File Transfer Protocol) – A simplified version of FTP used for transferring small files between devices.
Token Ring – An older networking protocol where a data token is passed around nodes in a ring topology.
Two-Factor Authentication (2FA) – An additional security layer requiring a second form of authentication.
Traceroute – A command-line tool that tracks the path data takes across a network.
Traffic Shaping – A technique used to control and prioritize network bandwidth usage.
Trojan Horse – Malware that appears legitimate but can harm or control a system.
Time-to-Live (TTL) – A value in network packets that defines how long they should exist before being discarded.
UDP (User Datagram Protocol) – A connectionless protocol used for fast data transmission, such as video streaming.
Uptime – The amount of time a network or system is operational without failure.
Virtual LAN (VLAN) – A logical grouping of devices within a network to improve security and efficiency.
Virtual Private Network (VPN) – A secure connection that encrypts internet traffic between a user and a remote network.
VoIP (Voice over Internet Protocol) – A technology that allows voice communication over the Internet.
Virus – A type of malicious software that spreads by infecting files and systems.
Vulnerability Scan – A security assessment that identifies weaknesses in a network or system.
Wi-Fi 6 – The latest generation of wireless technology that improves speed and performance.
Wireless Access Point (WAP) – A device that enables wireless devices to connect to a wired network.
WAN (Wide Area Network) – A network that connects multiple LANs across long distances.
WEP (Wired Equivalent Privacy) – An outdated wireless encryption protocol that WPA and WPA2 have replaced.
WPA3 (Wi-Fi Protected Access 3) – The latest wireless security protocol designed to improve encryption and authentication.
Zero Trust Security – A security model that requires continuous verification for network access.
Zombie Computer – A compromised computer controlled remotely to perform malicious tasks, such as launching DDoS attacks.
Zone-Based Firewall – A security feature that applies rules to different network zones for better protection.
Zigbee – A low-power wireless communication protocol used for IoT devices.
Z-Wave – A wireless protocol used in smart home and automation systems.
Frequently Asked Questions About Network Administrator Training
What is network administrator training, and why is it important?
Network administrator training teaches you to design, install, secure, and manage computer networks for businesses and organizations. It’s essential because it prepares you to prevent network failures, protect against cyber threats, and ensure smooth communication between devices and systems, critical for keeping modern businesses running.
How long does it take to complete network administrator training?
Most network administrator training programs take about 1 to 2 years to complete, depending on whether you pursue an associate degree, certification courses, or hands-on training. At Florida National University, the Network Systems Administrator program provides comprehensive training designed to quickly prepare you for entry-level roles.
How much can I earn after completing a network administrator training program?
Salaries for network administrators vary depending on experience, certifications, and location. On average, entry-level network administrators earn between $45,000 and $65,000 annually, while experienced professionals can make $75,000 to $100,000 or more. Network administrator training helps you qualify for these roles and boost your earning potential.
What jobs can I get with network administrator training?
With network administrator training, you can work as a Network Administrator, System Administrator, LAN Administrator, Network Technician, IT Support Specialist, or Help Desk Technician. These roles involve managing networks, securing data, and solving connectivity issues for businesses of all sizes.
Is network administrator training a good career path for the future?
Yes! Network administrator training leads to a stable, in-demand career in the IT industry. As businesses increasingly rely on technology, skilled network administrators are needed to keep systems secure and running smoothly. The field offers solid salaries, career growth, and opportunities to specialize in areas like cybersecurity or cloud networking.
Eager to Learn More about Networking Systems Administration?
This Networking System Administrator program provides students with technical training and foundational knowledge for designing, installing, configuring, and supporting computer networks. Our graduates are well-prepared for entry-level positions as System Administrators, Network Administrators, LAN Administrators, and Help Desk Support Specialists. The program also includes a fifteen-credit-hour component of General Education/Liberal Arts courses, offering the foundation necessary to continue onto a bachelor’s degree.
If you are interested in Information Technology, let Florida National University answer any questions you may have. Contact us today to learn more about our associate degree programs.